
Quotation For Security Services Sample Classles Democracy
Post Office Protocol. Allows a local email client to download an email from an remote email server. POP3 user agents (UA) connect via TCP to the server (typically. port 110) After authorization, the UA can issue POP3 commands to retrieve and delete mail. Internet Mail Access Protocol.
Cyber Security PowerPoint Template and Keynote Slide Slidebazaar
Slide 1 of 21. Email Security For Network Security Training Ppt. Presenting Email Security for Network Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations.
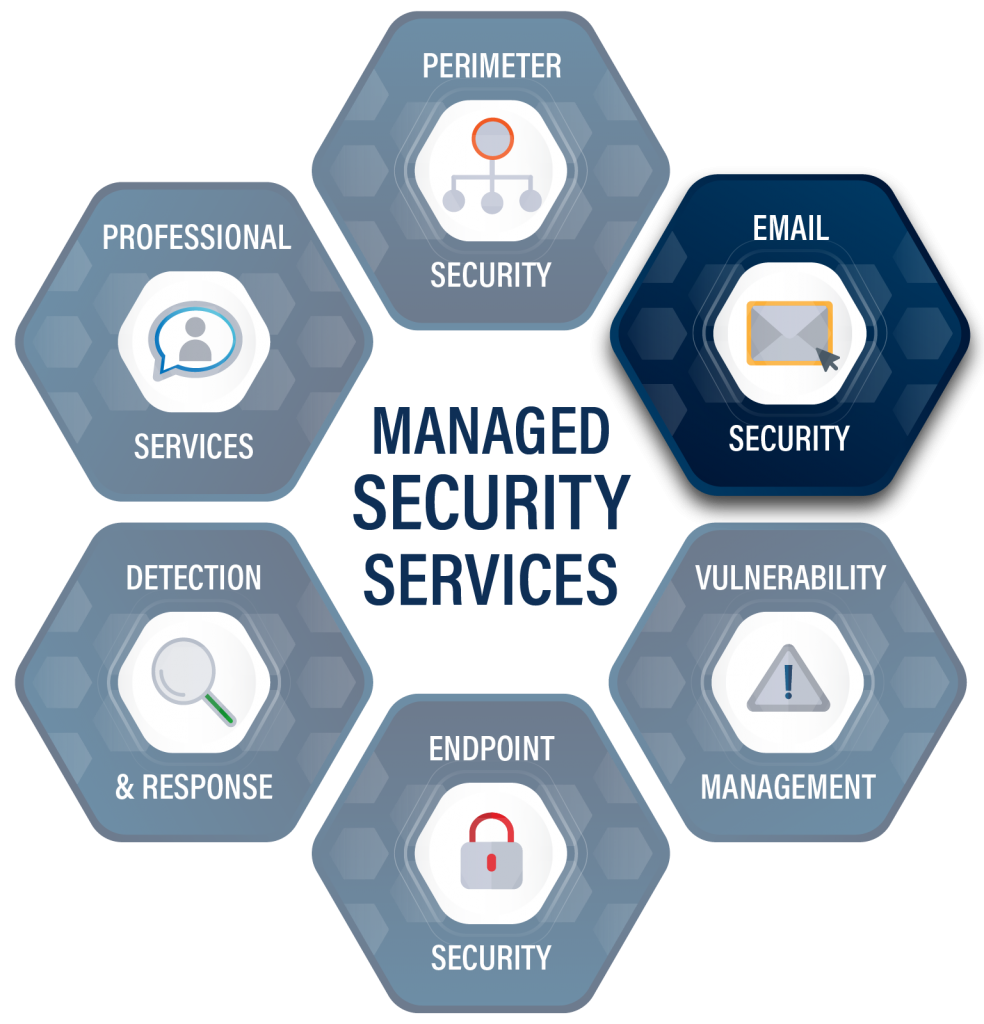
Managed Email Security Services Cybersecurity Solved Ascend Technologies
Email Security Presentation Slides. Email security is a crucial aspect of protecting sensitive information and preventing unauthorized access. With the increasing threat of cyberattacks, organizations must prioritize the implementation of robust email security measures. These may include advanced spam filtering, encryption, and authentication.

Complete Email Security & Solutions Reach IT
Reviews. Download our Email Security PPT template to describe various cybersecurity measures that keep the contents and access of an email account or service secure from unauthorized access. Cybersecurity experts and vulnerability analysts can take advantage of this 100% customizable deck to highlight the significance of these security measures.

Cyber Security Training Presentation Skillcast
100% customizable slides and easy to download. Slides are available in different nodes & colors. The slides contain 16:9 and 4:3 formats. Easy to change the colors quickly. It is a well-crafted template with an instant download facility. Compatible with Google Slides and PowerPoint. This slide is designed with a creative design with a text area.

What You Need to Know About Email Security in 2016 Business 2 Community
Slide 1 of 10. Email Phishing And Digital Security Icon. Slide 1 of 4. Global security email and data protection phone security ppt icons graphics. Slide 1 of 6. Cyber Security Policy Email And Chat Policy Objective And Guidelines. Slide 1 of 2. Secure email cloud services ppt powerpoint presentation model vector cpb.

Email Security by Darktrace AG Philippines Inc.
Email security defined. Email security is the practice of protecting email accounts and communications from unauthorized access, loss, or compromise. Organizations can enhance their email security posture by establishing policies and using tools to protect against malicious threats such as malware, spam, and phishing attacks.

Ultimate Guide to Email Security/ Best Email Security Practices/Email Security All You Wanted
Encrypted mail 1. The user writes the message as clear-text. 2. A random session key is being created (tripleDES [6] or RC2 [7]) 3. The message is being encrypted using the random session key. 4. For every recipient, the session key is being encrypted using the recipient's public key (DH [8] or RSA [5]).

Mimecast Email Security and Cyber Resilience
Email Security and Awareness. Oct 10, 2013 • 7 likes • 8,955 views. Download Now. Download to read offline. Technology Business. Email as used in personal and corporate work which impacts data risks, availability, business objectives failures, Good and bad practices. Sanjiv Arora CISA, CHPSE, Cyber Risk and Compliance Consultant at People.

How having an Email Back Up keeps your Business Compliant Business Computer Solutions
Email Security Definition. Email security helps protect an organization's attack surface from cyber threats that use email account attack vectors such as phishing and spam to gain unauthorized access to the network. By following email security best practices for cybersecurity including email accounts, organizations can reduce the spread of.

Email Security Best Practices
Presenting our Email Security Solution Industry Report PowerPoint Presentation Slides. This is a completely adaptable PPT slide that allows you to add images, charts, icons, tables, and animation effects according to your requirements. Create and edit your text in this 100% customizable slide.

Introducing the Microsoft 365 Email Security Checklist ITProMentor
Presenting this set of slides with name email security vector icon ppt powerpoint presentation model example topics. This is a four stage process. The stages in this process are email security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Email Security Information Security Ppt Powerpoint Presentation Inspiration Samples Cpb
Email Security Definition. Email security involves the strategic set of measures and techniques used to protect email-based communications, effectively preserving the confidentiality, integrity, and availability of email messages. As a critical safeguard for all types of organizations and professionals, email security prevents unauthorized.
How to Improve your Email Security — Your Technology Elevated
Email security presentation. 1. Email Security 1. 2. Introduction Electronic mail or, simply Email is the most widely used and regarded network services Currently message contents are not safe- May be inspected either in transit Or by suitably privileged users on destination system 2. 3.

Security Tip Tuesday Email Security Shred Boss
Cyber security experts, security consultants, and software security engineers can leverage these fantastic PowerPoint slides to display the benefits of email security for enterprises device access control, real-time threat protection, etc. You can also show the risks and best practices of email security.

Network Security Presentation
Freepik. Flaticon. Slidesgo. Wepik. Videvo. We assure you that your presentation will be a success thanks to these Google Slides and PPT templates on security. Free Easy to edit Professional.